Shubham Sharma on Twitter: "Best of Cyber Security Tools #infosec # cybersecurity #pentesting #oscp #informationsecurity #hacking #cissp #redteam #technology #DataSecurity #CyberSec #Hackers #tools #bugbountytips #Linux #websecurity #Network ...

Cyber Security Tools And Techniques Ppt PowerPoint Presentation Styles Vector - PowerPoint Templates

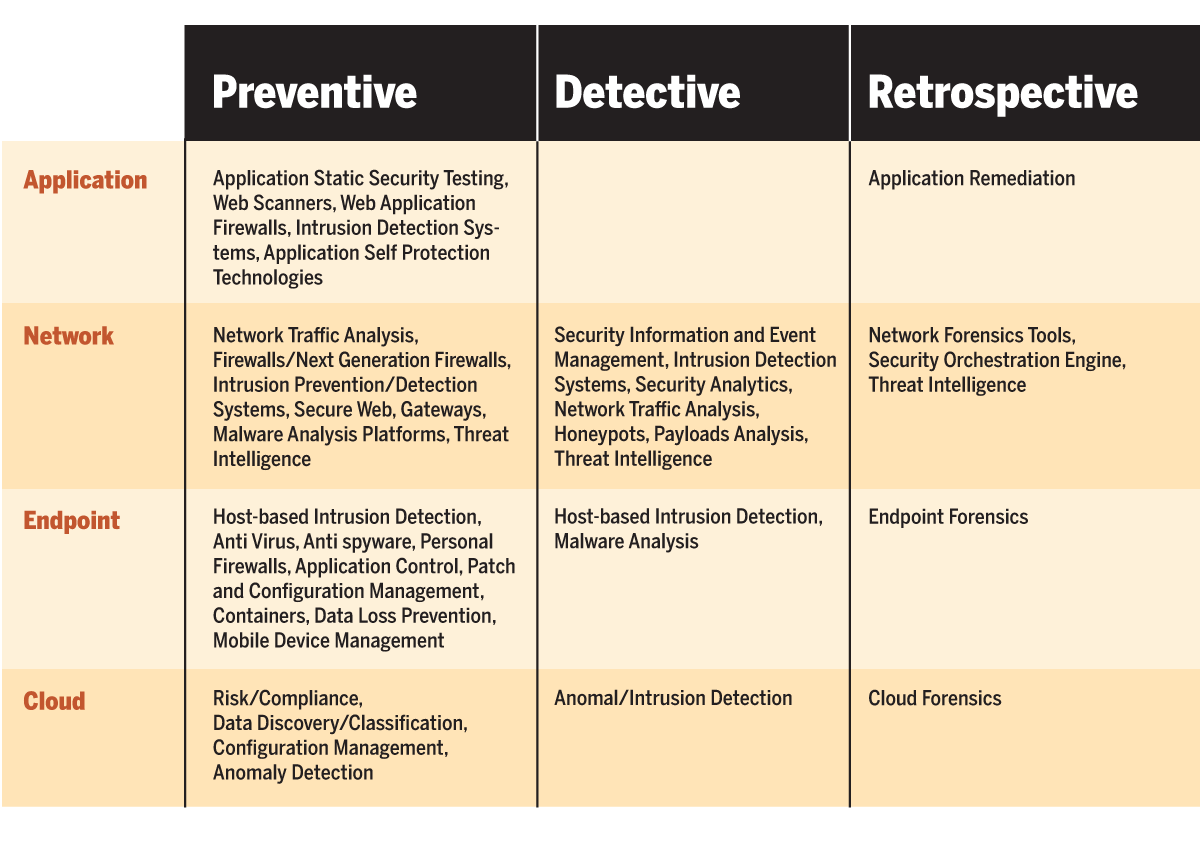
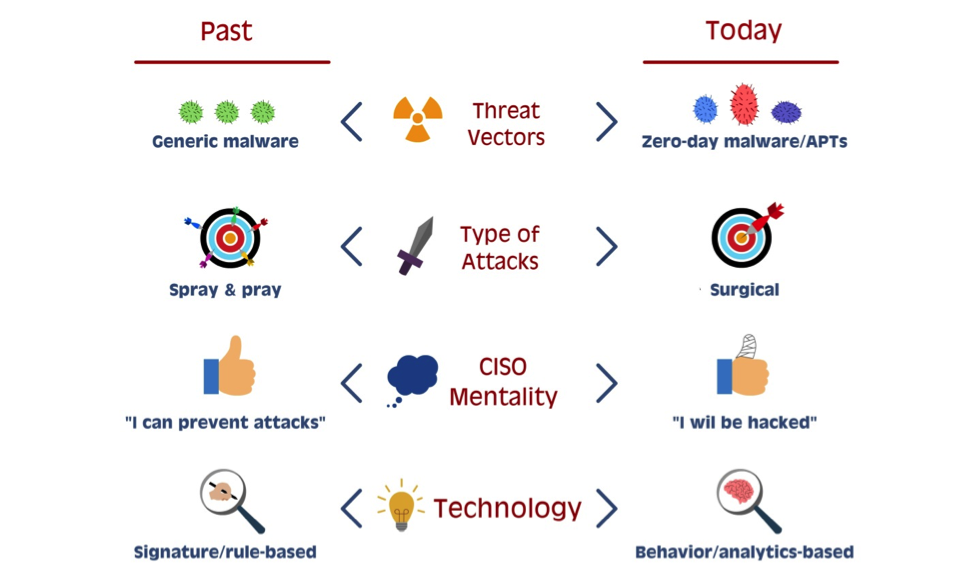
Cybersecurity Tools: Too Much of a Good Thing? | ITPro Today: IT News, How-Tos, Trends, Case Studies, Career Tips, More





![What tools are used for offensive security? - Applied Network Security [Book] What tools are used for offensive security? - Applied Network Security [Book]](https://www.oreilly.com/api/v2/epubs/9781786466273/files/assets/image_17_001.png)