
Know the encrypted and decrypted message key cry.ptography encryption decryption qu.estions - YouTube
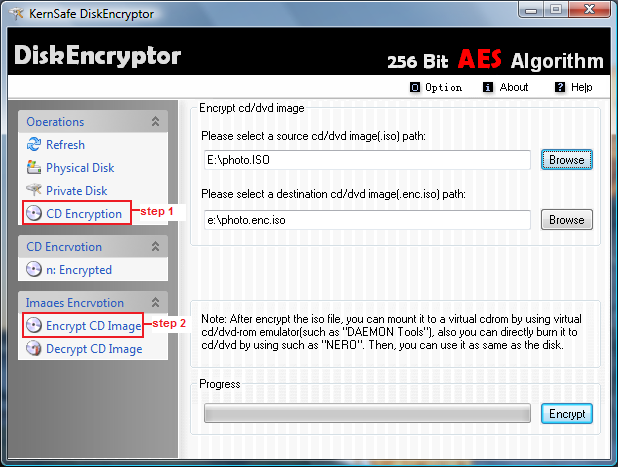
Encrypt CD image This section describes how to encrypt and decrypt a image file. 1. Click Start > Programs >KernSafe> DiskEncryptor>DiskEncryptor; to start up DiskEncryptor; 2. Select CD Encryption under Operations,and then choose Encrypt CD Image ...

An efficient public-key searchable encryption scheme secure against inside keyword guessing attacks - ScienceDirect










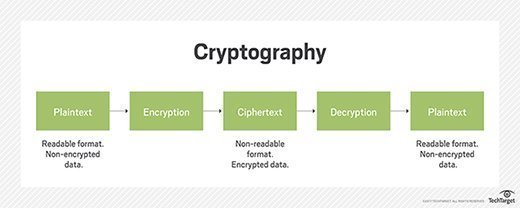
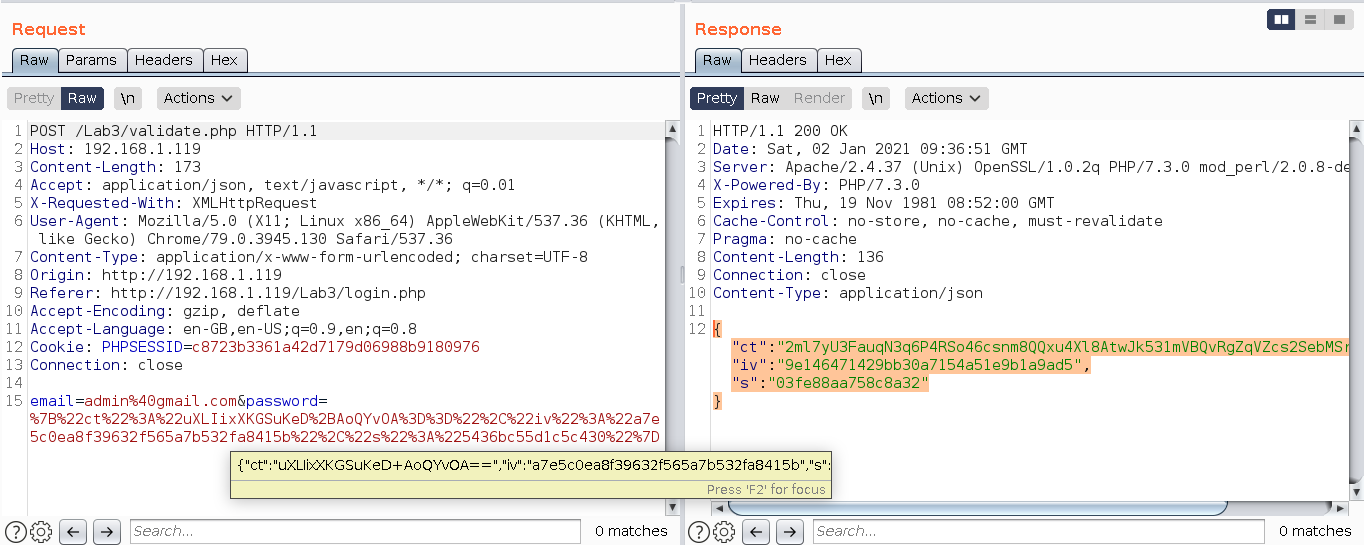
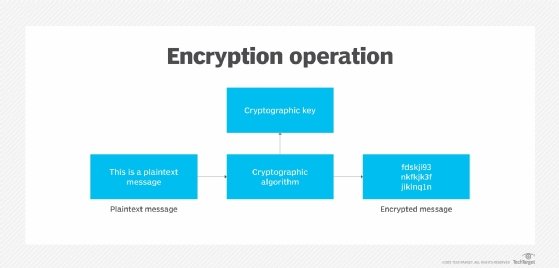
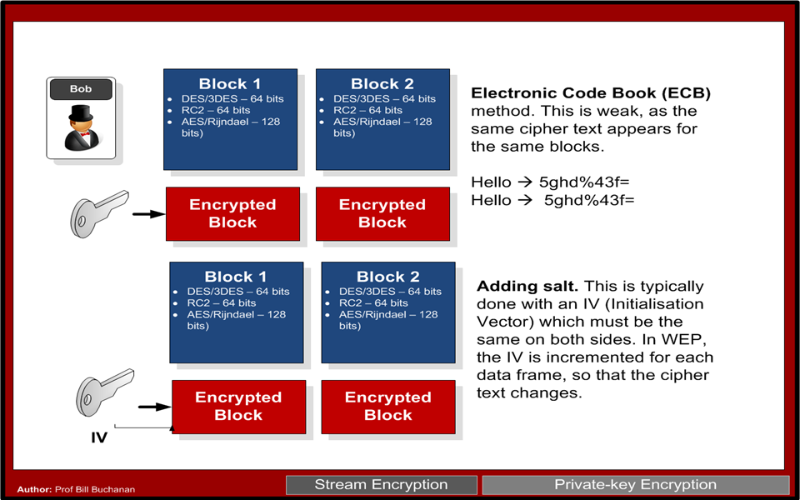
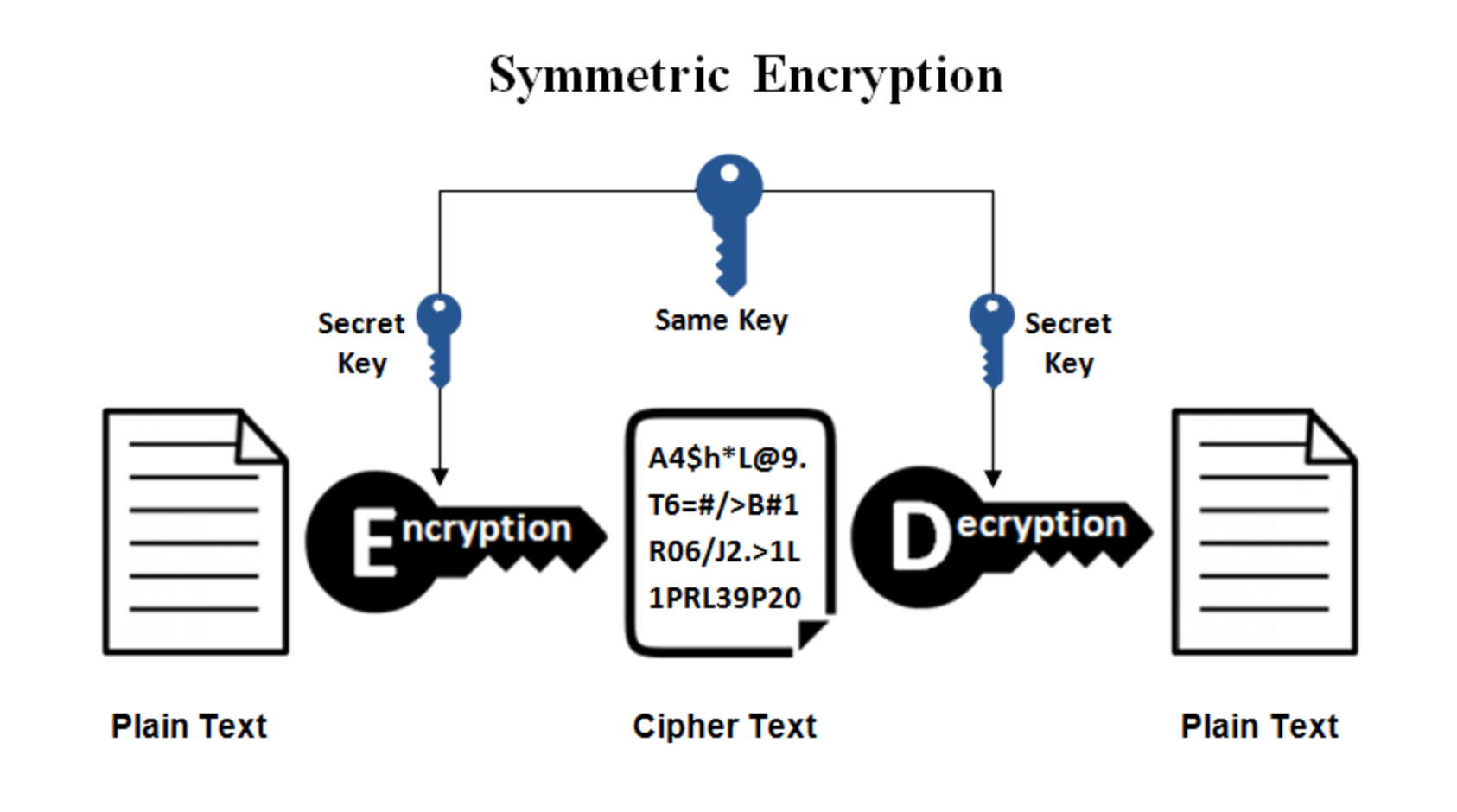


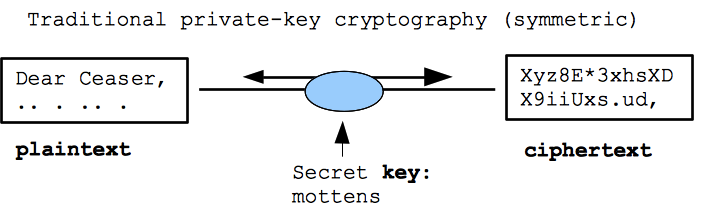



![Chapter 6] 6.2 What Is Encryption? Chapter 6] 6.2 What Is Encryption?](http://web.deu.edu.tr/doc/oreily/networking/puis/figs/puis_0601.gif)